System and Software Engineering
BROWSE TOPICS
Introduction to System and Software Engineering
System and software engineering are the cornerstones of modern technological development. System engineering focuses on designing and managing complex systems over their life cycles, ensuring that all components of a system work together seamlessly. Software engineering is a branch of engineering concerned with developing software applications, ensuring that they are reliable, maintainable, and scalable.
In today’s technology-driven world, system and software engineering solutions are essential in building innovative, reliable, and efficient software systems that power industries ranging from healthcare to aerospace. These engineering approaches ensure the delivery of high-quality solutions, making them integral to modern product development, infrastructure management, and operational processes.
Key Concepts in System and Software Engineering
In system and software engineering, several key concepts form the foundation for successful project development and management:
System Architecture: This is the blueprint that defines the structure, behavior, and interaction of components within a system. A well-architected system ensures all components work together smoothly, promoting efficiency, scalability, and reliability.
Requirements Engineering: This involves gathering, analyzing, and documenting the needs and expectations for a system. It ensures both functional (what the system should do) and non-functional (performance, security) requirements are clearly defined and met.
Design Principles: In software development, design principles like modularity (breaking down into smaller components), separation of concerns (handling different functionalities independently), and reusability (using components across different projects) are crucial for building scalable and maintainable systems.
Quality Assurance (QA): QA ensures that the software meets specific standards for reliability, performance, and security. It involves testing at various stages to identify defects and ensure the software works as expected.
Software Development Methodologies: Approaches like Waterfall, Agile, and DevOps guide how projects are managed:
Waterfall follows a linear, step-by-step approach, with each phase completed before the next begins.
Agile emphasizes iterative development, flexibility, and close collaboration between teams.
DevOps integrates development and operations to automate deployment and ensure continuous delivery.
These key concepts ensure efficient, reliable, and successful system and software engineering projects.
System and Software Development Lifecycle (SDLC)

The System and Software Development Lifecycle (SDLC) outlines the critical stages that every system or software project must go through, ensuring a structured approach to development. Each phase contributes to delivering a reliable, efficient, and maintainable solution:
- Requirements Analysis: This is the first phase where the project’s objectives are identified. It involves working closely with stakeholders to understand and document the functional (what the system should do) and non-functional requirements (performance, security, etc.). Clear requirements help set the foundation for the project’s success.
- Design: In this phase, a blueprint for the system or software is created. It includes planning the architecture, components, data flow, and interfaces, ensuring that the design meets both technical and business requirements. This phase outlines how the system will be built.
- Development: The actual coding happens here. Developers write the code based on the design specifications, turning ideas into a working software or system. This phase requires collaboration among development teams and often involves multiple iterations.
- Testing: After development, testing is critical to ensure that the system works as intended. This phase involves verifying functionality, performance, security, and identifying any bugs or issues. Different types of testing (unit, integration, system, and acceptance) are conducted to ensure the system meets its requirements.
- Deployment: Once the system has passed testing, it is moved to the production environment, making it available to users. This phase may include finalizing configurations, data migrations, and user training. Deployment must be carefully managed to minimize disruptions.
- Maintenance: After deployment, ongoing maintenance is required to ensure the system remains up-to-date, secure, and bug-free. This includes providing user support, fixing any new issues, and making improvements or updates as needed.
Successfully managing a project through the SDLC involves strong project management, aligning teams, timelines, and resources, along with strategic planning and technical execution to deliver a high-quality solution.
System and Software Requirements Engineering is a crucial discipline within the software and system development process. It ensures that the final product aligns with both business objectives and user needs, minimizing rework and maximizing project success. This process revolves around the identification, analysis, documentation, and validation of the requirements that the system or software must meet. Each step plays a key role in creating a product that is both functional and efficient.
Key Techniques in Requirements Engineering:
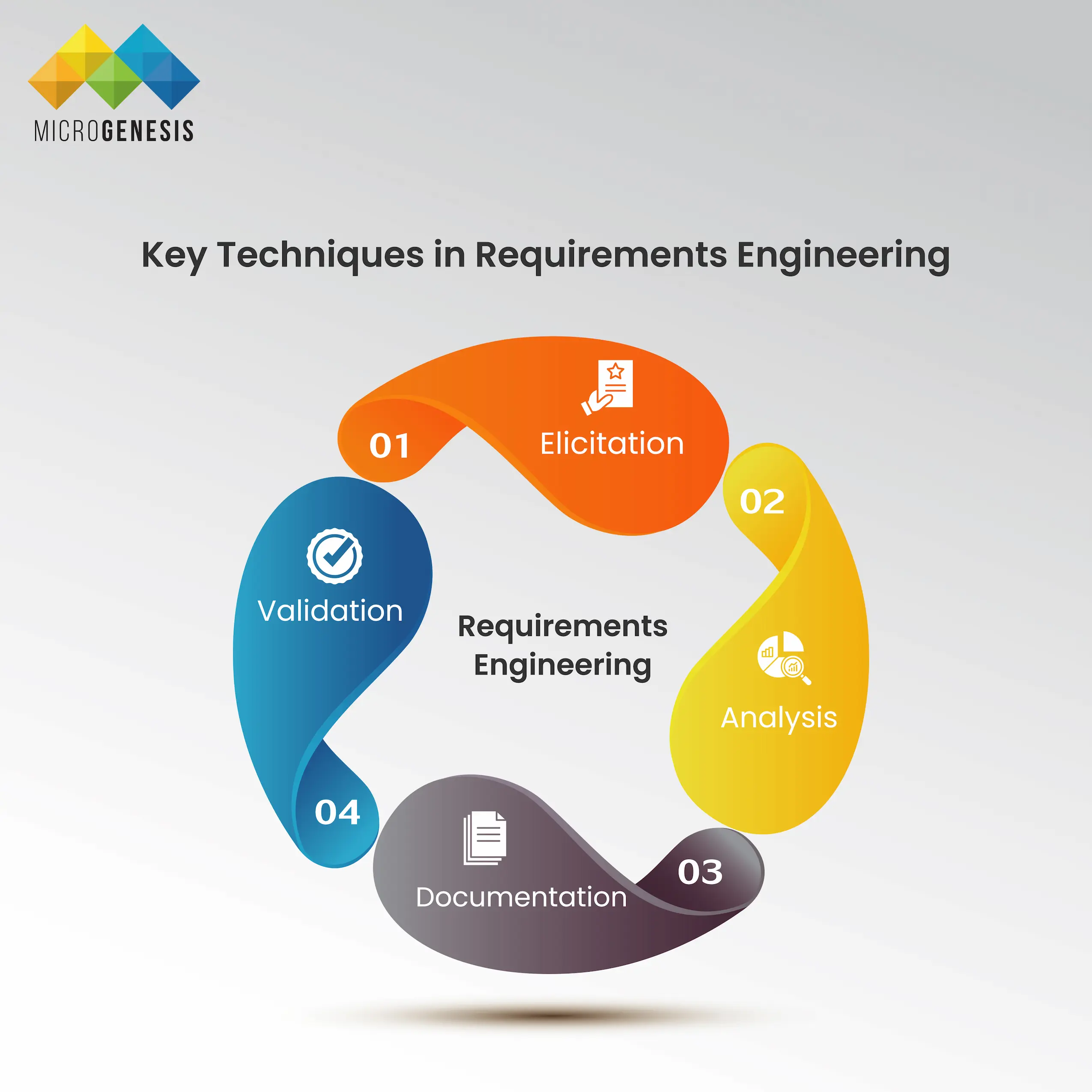
1. Elicitation:
a. Purpose: The first step in requirements engineering, elicitation focuses on gathering information from stakeholders to understand their needs, expectations, and constraints. The goal is to identify what the system or software must achieve and which problems it needs to solve.
b. Methods: Elicitation can involve various methods such as:
i. Interviews: Direct conversations with stakeholders to gather in-depth information.
ii. Workshops: Collaborative sessions where teams work together to discuss and refine requirements.
iii. Surveys and Questionnaires: Gathering data from a broader audience to capture diverse viewpoints.
iv. Observation: Studying how users currently interact with similar systems to identify pain points and areas for improvement.
c. Challenges: A significant challenge in this phase is dealing with conflicting stakeholder needs, vague requirements, or discovering hidden requirements later in the development cycle.
2. Analysis:
a. Purpose: Once the requirements are gathered, the next step is analyzing them to ensure they are complete, clear, and feasible. The focus here is on understanding the relationships between different requirements, identifying any conflicts or dependencies, and ensuring that all requirements are aligned with business goals.
b. Activities:
i. Prioritization: Determining which requirements are most critical to the system’s success and should be addressed first.
ii. Feasibility Studies: Ensuring that the gathered requirements are technically feasible and within the project’s scope and budget.
iii. Modeling: Creating visual representations (e.g., use case diagrams, flowcharts) to better understand system functionality and relationships between requirements.
c. Outcome: The result is a refined set of requirements that are clearly defined and structured to guide the development team in their work.
3. Documentation:
a. Purpose: Proper documentation ensures that the requirements are clearly outlined and accessible to all stakeholders. This document acts as a blueprint for the development process, guiding the design, development, and testing teams.
b. Content:
i. Functional Requirements: Define what the system should do (features, behaviors).
ii. Non-Functional Requirements: Define how the system should perform (speed, security, reliability).
iii. Constraints: Document limitations such as budget, technology choices, or compliance requirements.
c. Formats: Requirements documents can vary from simple text-based specifications to complex models depending on the project needs. Common documentation standards include Software Requirements Specifications (SRS) or user stories in Agile development.
4. Validation:
a. Purpose: After the requirements are documented, validation ensures that they accurately reflect stakeholder needs and are ready for development. This step aims to confirm that the documented requirements align with business goals and that stakeholders agree on what is being built.
b. Techniques:
i. Prototyping: Creating a visual or functional prototype allows stakeholders to review and provide feedback early in the process.
ii. Walkthroughs and Reviews: Conducting structured reviews with stakeholders to ensure the documented requirements meet their expectations.
iii. Test Cases: Writing test cases based on the requirements ensures that, once developed, the system will be tested for adherence to those requirements.
c. Outcome: Validated requirements reduce the risk of miscommunication and misunderstandings. This step also ensures that all stakeholders have a shared understanding of the system’s goals and features before development begins.
Benefits of Effective Requirements Engineering:
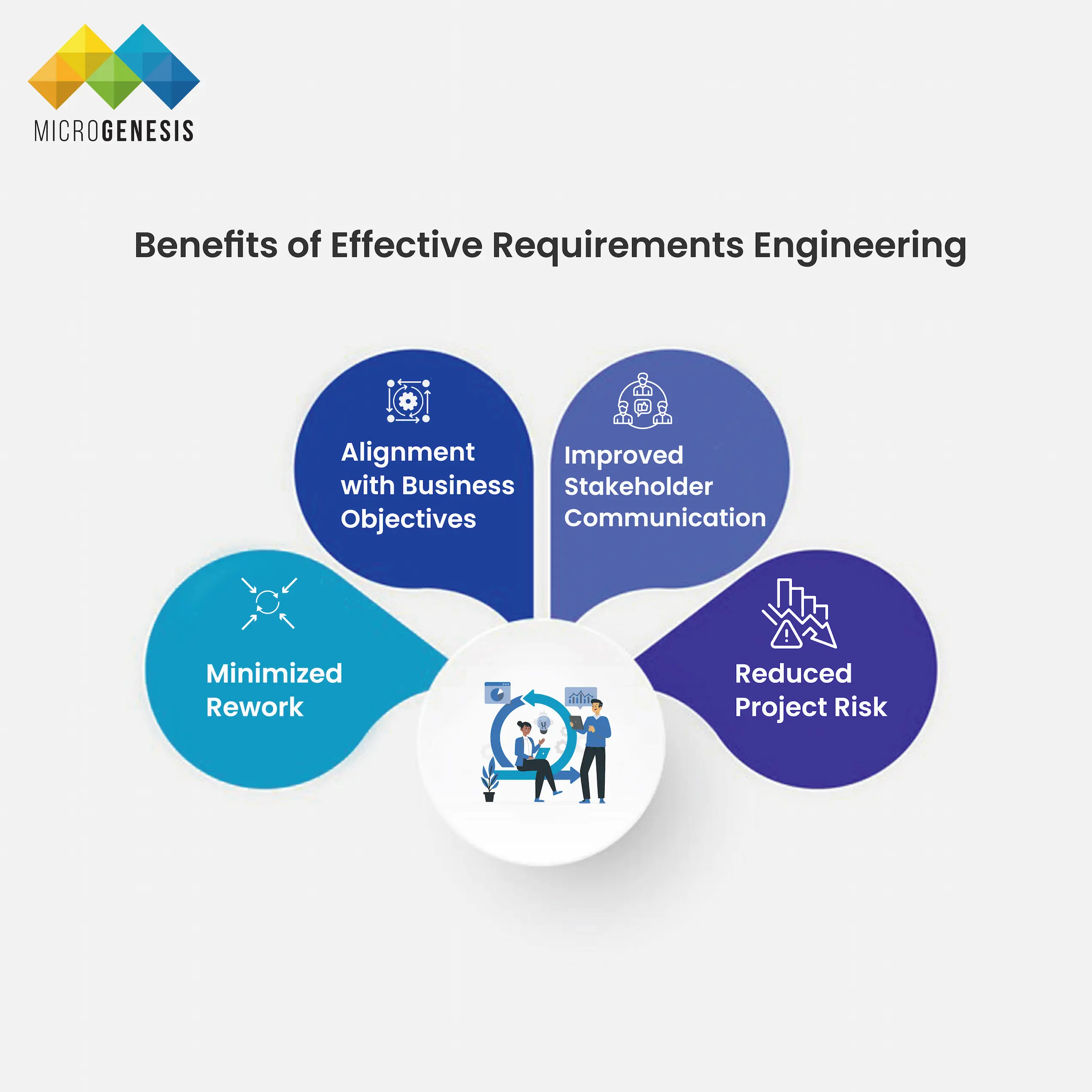
- Minimized Rework: By clearly defining and validating requirements early, there’s less risk of discovering errors or omissions later in the development cycle, which can lead to costly rework.
- Alignment with Business Objectives: Proper requirements engineering ensures that the system or software aligns with business goals, increasing the likelihood of delivering a successful product.
- Improved Stakeholder Communication: Regular validation and documentation ensure that all parties involved have a common understanding of the project’s goals, reducing the risk of misaligned expectations.
- Reduced Project Risk: A structured approach to requirements minimizes the risk of scope creep, budget overruns, and timeline delays.
By focusing on gathering, analyzing, documenting, and validating the system’s needs, requirements engineering ensures a clear path from project conception to delivery. It fosters collaboration between stakeholders and the development team, reducing misunderstandings and building a solid foundation for success.
System and Software Design Principles
System and Software Design Principles provide the foundation for creating scalable, maintainable, and secure systems and software. These principles guide developers and architects in structuring software in a way that makes it easy to understand, test, and modify, ensuring long-term success and adaptability. Key design principles include:
1. Modularity:
-
- Definition: Modularity is the practice of breaking down a system or software into smaller, self-contained components or modules that can be developed, tested, and maintained independently.
- Benefits:
- Easier troubleshooting: If an issue arises, developers can isolate the problem to a specific module without affecting the entire system.
- Parallel development: Multiple modules can be worked on simultaneously by different teams, improving development efficiency.
- Reusability: Modules can be reused across different projects, reducing redundant work.
- Example: In a large-scale e-commerce system, the payment module, user authentication module, and product catalog can be developed as independent units.
2. Separation of Concerns:
-
- Definition: Separation of concerns is a design principle that advocates for organizing a system so that distinct concerns, or functionalities, are isolated into separate components. Each component handles one aspect of the system without overlapping into others.
- Benefits:
- Simplifies code: Each part of the system deals with a single concern, making the codebase easier to understand and maintain.
- Flexibility: Changes to one concern (e.g., UI) do not affect other parts of the system (e.g., business logic), making updates more manageable.
- Example: In a web application, the user interface (UI) is separate from the business logic and data storage layers, making it easier to update the front-end without disrupting the back-end.
3. Design Patterns:
-
- Definition: Design patterns are standardized, reusable solutions to common design problems that arise during software development. They are templates that can be adapted to solve particular problems, ensuring consistency and reliability in the design process.
- Common Patterns:
- Model-View-Controller (MVC): A pattern used in web applications that separates the application into three components: the model (data), the view (UI), and the controller (logic), allowing for better separation of concerns and more manageable code.
- Singleton Pattern: Ensures that a class has only one instance and provides a global point of access to that instance. Useful in resource management (e.g., database connections).
- Factory Pattern: Provides an interface for creating objects, allowing subclasses to alter the type of objects that will be created without changing the client code.
- Benefits:
- Efficiency: Design patterns offer proven solutions, saving time during development.
- Consistency: Teams can follow familiar patterns, reducing misunderstandings and improving collaboration.
- Maintainability: Since design patterns are well-documented, they enhance the readability and future maintainability of the code.
4. Scalability:
-
- Definition: Scalability refers to a system’s ability to handle increased loads, whether in terms of users, data, or transactions, without compromising performance.
- Design Considerations:
- Architect systems to be horizontally scalable, meaning additional servers or resources can be added to handle more load.
- Use load balancing and distributed systems to spread workloads across multiple resources.
- Example: Cloud-based systems that can automatically scale resources based on traffic demand, such as increasing server instances during peak usage.
5. Maintainability:
-
- Definition: Maintainability focuses on designing systems that are easy to update, fix, and extend over time. The goal is to reduce the complexity of future modifications and improve the lifespan of the software.
- Best Practices:
- Write clean, well-documented code to help developers understand the system easily.
- Apply the DRY (Don’t Repeat Yourself) principle to avoid code duplication and reduce maintenance effort.
- Ensure modularity and separation of concerns to make code easier to manage.
6. Security by Design:
-
- Definition: Security should be integrated into the design phase of system and software development to protect against vulnerabilities and attacks from the outset.
- Key Practices:
- Use encryption and secure authentication methods.
- Perform regular code reviews to identify potential security vulnerabilities.
- Design for the principle of least privilege, ensuring users only have access to the resources they need.
- Example: In a financial system, secure design practices like data encryption and role-based access control (RBAC) ensure the safety of sensitive data and reduce the risk of breaches.
Good Design Practices: Adhering to these principles allows developers to create systems and software that are flexible and adaptable to changes. Well-designed systems:
-
- Can be easily modified and extended with new features or updates.
- Are easier to debug and maintain.
- Perform efficiently, even under increased loads.
- Are resistant to security threats, reducing the risk of future vulnerabilities.
Ultimately, following these design principles ensures that software solutions are robust, scalable, and built for longevity.
Quality Assurance and Testing in System and Software Engineering
Quality Assurance (QA) and Testing are critical aspects of the software and system development process, ensuring that the product meets both functional and non-functional requirements. QA encompasses a variety of testing practices designed to identify and fix issues early, maintain performance standards, and secure the system before deployment.
Without comprehensive testing, even minor issues can escalate into serious problems, leading to system failures, costly downtime, and potential security breaches. Effective QA helps avoid these risks, ensuring that the software or system operates smoothly and reliably once it reaches the end user.
Types of Testing:
1. Unit Testing:
- Definition: Unit testing focuses on verifying the functionality of individual components or modules of a system. Each module is tested separately to ensure that it works as expected in isolation before being integrated with other parts of the system.
- Goal: Catch bugs early in the development process, preventing issues from spreading across the system.
- Example: Testing a function in a payment processing system to ensure that it calculates the correct total for a purchase.
2. Integration Testing:
- Definition: Integration testing ensures that different components or modules of a system work together as intended. After individual components pass unit testing, integration testing verifies the interaction between them.
- Goal: Identify and resolve issues related to data flow and interaction between different parts of the system.
- Example: Testing the integration of the payment gateway with the shopping cart module in an e-commerce platform.
3. System Testing:
- Definition: In system testing, the entire system is tested as a whole. This includes testing all integrated components to ensure they function together as expected. System testing is designed to verify that the product meets the specified requirements.
- Goal: Ensure that the system operates correctly in an environment similar to the production environment.
- Example: Testing an e-commerce system’s functionality, including browsing, adding items to the cart, checkout, and payment processing, to ensure that all features work seamlessly.
4. Acceptance Testing:
- Definition: Acceptance testing is the final phase of testing, where the system is evaluated to ensure it meets the needs of the end-users and stakeholders. This testing is often performed by users or business stakeholders to verify that the software works as expected in real-world scenarios.
- Goal: Confirm that the system is ready for deployment and meets all business objectives.
- Example: Testing an online banking platform to ensure that customers can successfully transfer funds, pay bills, and access account information as they would in real use.
The Importance of QA and Testing:
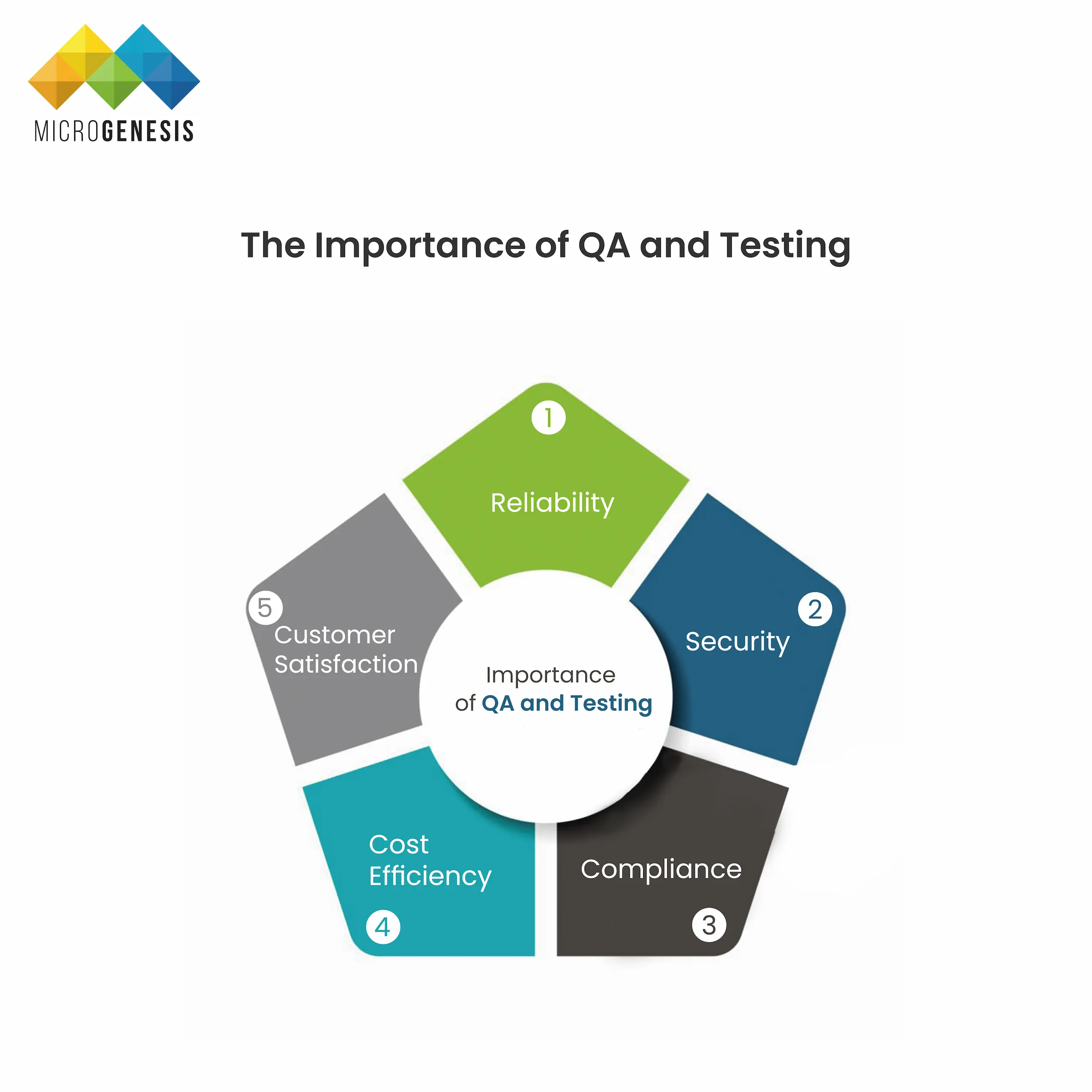
- Reliability: QA ensures that the system or software performs consistently under different conditions. Rigorous testing can catch issues before they affect end users, ensuring the product is stable and reliable.
- Security: In today’s digital landscape, security vulnerabilities are a major concern. QA processes, including security testing, help identify and resolve potential threats, reducing the risk of data breaches and cyberattacks.
- Compliance: Many industries, such as healthcare and finance, have strict regulatory requirements. QA ensures that the software complies with relevant laws and industry standards, avoiding costly fines or legal issues.
- Cost Efficiency: Fixing bugs and issues early in the development process is far less expensive than addressing them after deployment. QA reduces the overall cost of development by minimizing the need for costly rework or fixes later in the project lifecycle.
- Customer Satisfaction: A well-tested product leads to a positive user experience, resulting in higher customer satisfaction, fewer complaints, and greater trust in the brand.
In conclusion, QA and testing are essential to delivering high-quality software that meets business and user requirements. By employing different testing techniques, organizations can ensure that their systems are robust, secure, and ready for real-world use.
System and Software Configuration Management
System and Software Configuration Management is essential for ensuring the consistency, integrity, and reliability of software systems, especially as they evolve over time. It involves a set of practices and tools that help manage and track changes to software components, ensuring that all modifications are controlled and well-documented. Without effective configuration management, software can become unstable or inconsistent, making troubleshooting and maintenance difficult.
Here are the key aspects of configuration management:
1. Version Control:
-
- Definition: Version control systems are tools that allow developers to track and manage changes to source code or system configurations over time. They provide a detailed history of changes, making it easier to revert to previous versions if needed and to collaborate with other team members.
- Popular Tools: Git, Subversion (SVN), Mercurial.
- Benefits:
- Collaboration: Multiple developers can work on the same project simultaneously without overwriting each other’s changes.
- Rollback: If a new change introduces a bug, the system can easily be rolled back to a previous, stable version.
- Branching and Merging: Developers can work on different features or bug fixes in separate branches, then merge changes back into the main codebase when they’re ready.
- Example: In an enterprise software project, version control tools like Git allow teams to manage multiple versions of the software while keeping track of updates and changes made by different developers.
2. Change Management:
-
- Definition: Change management is the process of requesting, evaluating, and approving modifications to a system or software project. It ensures that changes are deliberate and evaluated for potential impacts on the system’s functionality, security, and stability.
- Steps in Change Management:
- Change Request: The change process begins with submitting a formal change request, detailing the proposed modification, reasons, and potential impact.
- Evaluation: The proposed change is reviewed and analyzed to determine its feasibility, risks, and benefits.
- Approval: Based on the evaluation, the change is either approved or rejected by stakeholders.
- Implementation: If approved, the change is implemented following a structured process.
- Review: Post-implementation, the change is reviewed to ensure it has achieved the desired result without introducing any new issues.
- Benefits:
- Reduced Risk: Ensures that changes are carefully considered and planned to minimize the risk of unintended consequences.
- Transparency: Provides a clear audit trail of who approved the change and why, making it easier to track responsibility.
- Consistency: Ensures changes are made in a controlled and structured manner, reducing the likelihood of errors or inconsistencies.
- Example: In a banking application, a change management process would be essential when introducing a new feature, such as adding two-factor authentication, to ensure it doesn’t disrupt existing services.
3. Release Management:
-
- Definition: Release management coordinates and oversees the deployment of new software updates, features, or patches. It ensures that changes are introduced smoothly, without disrupting the existing operations or causing system downtime.
- Stages of Release Management:
- Planning: Defining what will be included in the release and establishing a timeline for implementation.
- Development: Creating the new feature or update in a controlled environment.
- Testing: Ensuring the release is thoroughly tested for quality, performance, and security.
- Deployment: Deploying the update to the live environment in a way that minimizes disruption to users.
- Monitoring: Observing the system post-deployment to catch any potential issues or performance degradation.
- Benefits:
- Controlled Deployment: Reduces the risk of errors or issues during the deployment of new updates.
- Rollback Plans: Allows for the quick reversal of updates in case problems arise during or after deployment.
- End-User Satisfaction: Ensures new features or changes are introduced smoothly, reducing frustration for users.
- Example: In a SaaS platform, release management would ensure that updates are deployed during off-peak hours and that users are notified of any new features or changes, minimizing disruptions.
The Importance of Configuration Management

-
- Consistency: By managing changes in a structured way, configuration management ensures that systems remain consistent over time, even as updates and improvements are made.
- Documentation: Configuration management tools track every change, including who made the change and why. This creates a clear record that helps with debugging, auditing, and compliance with regulatory requirements.
- Collaboration: In large projects involving multiple teams, configuration management ensures everyone is working on the latest version of the system and that changes don’t conflict with each other.
- Minimizing Errors: By controlling how and when changes are made, configuration management reduces the likelihood of errors being introduced into the system.
In conclusion, system and software configuration management is vital for ensuring that software systems remain stable, consistent, and reliable throughout their lifecycle. By employing version control, change management, and release management practices, organizations can handle the complexities of modern software development while minimizing the risks associated with change.
System and Software Deployment and Maintenance
System and Software Deployment and Maintenance are crucial phases in the software development lifecycle (SDLC), ensuring that systems and applications are made available to end-users in a stable and efficient manner. Deployment marks the transition of software from a development environment to a production environment, while maintenance ensures the system remains functional, secure, and up to date over time.
Here are the key strategies and practices in deployment and maintenance:
1. Deployment:
-
- Definition: Deployment is the process of moving a system or software application from the development environment, where it is built and tested, to a live production environment where it is accessible to end-users. It is a critical step because any errors in deployment can result in system failure, user disruption, or security vulnerabilities.
- Phases of Deployment:
- Planning: Identifying which version of the software will be deployed, the timing of the deployment, and any potential impacts on users.
- Preparation: Ensuring the production environment is ready for deployment, including configuring servers, databases, and infrastructure.
- Execution: Moving the software from development to production, either manually or through automated tools.
- Verification: Testing the deployed system in the production environment to ensure that it works as expected.
- Challenges in Deployment:
- Risk of system downtime or disruption for end-users.
- Potential bugs or incompatibilities that were not caught during the testing phase.
- Coordination between different teams, including developers, operations, and business stakeholders.
2. Continuous Deployment:
-
- Definition: Continuous Deployment (CD) is an automated process that allows new features, bug fixes, and updates to be deployed to production frequently, often several times a day. It is part of the broader DevOps strategy, which emphasizes the automation of the software development and deployment process to improve speed, collaboration, and reliability.
- Benefits:
- Faster Release Cycles: CD allows teams to deploy updates quickly and frequently, providing end-users with new features and fixes faster.
- Reduced Human Error: Automation reduces the risk of errors during the deployment process, ensuring consistent, repeatable results.
- Greater Agility: Continuous deployment enables teams to respond to changes in business needs or user feedback more effectively.
- Tools: Jenkins, GitLab CI/CD, CircleCI, and Bamboo are popular tools used to automate the continuous deployment process.
- Example: In an e-commerce platform, continuous deployment can be used to regularly release new features like product recommendations, updates to payment gateways, or security patches, ensuring that users always have access to the latest functionality.
3. Monitoring and Maintenance:
-
- Monitoring: After deployment, it’s important to continuously monitor the performance of the system or software to ensure that it functions as expected. Monitoring tools provide real-time data about the health of the system, including server performance, network activity, error logs, and user behavior.
- Tools for Monitoring: Prometheus, Nagios, Datadog, and Splunk are common tools for system monitoring.
- Benefits: Early detection of issues, such as performance bottlenecks or security vulnerabilities, allows teams to address problems before they affect end-users.
- Proactive Monitoring: By analyzing data from monitoring tools, teams can proactively make adjustments, such as scaling infrastructure or optimizing code, to ensure the system remains stable under changing conditions.
- Monitoring: After deployment, it’s important to continuously monitor the performance of the system or software to ensure that it functions as expected. Monitoring tools provide real-time data about the health of the system, including server performance, network activity, error logs, and user behavior.
- Maintenance:
- Definition: Maintenance refers to the ongoing process of updating and optimizing a system or software application to ensure it remains secure, functional, and relevant to users over time. Maintenance is necessary to address bugs, implement patches, upgrade components, and optimize performance.
- Types of Maintenance:
- Corrective Maintenance: Fixing bugs or issues that arise after deployment.
- Adaptive Maintenance: Modifying the system to work in new environments or with updated hardware/software.
- Perfective Maintenance: Improving performance, usability, or functionality based on user feedback or evolving requirements.
- Preventive Maintenance: Making proactive changes to avoid future issues, such as updating libraries or addressing potential security vulnerabilities.
4. Best Practices in DevOps:
DevOps is a set of practices that automates and integrates the processes of software development and IT operations. It emphasizes collaboration, communication, and automation to streamline the deployment and maintenance process.
-
- Automation: Automating repetitive tasks like testing, deployment, and infrastructure configuration reduces the risk of errors and speeds up the release cycle.
- Collaboration: DevOps fosters close collaboration between development and operations teams, ensuring smoother deployments and faster problem resolution.
- Continuous Integration/Continuous Deployment (CI/CD): CI/CD pipelines automate the process of integrating code changes and deploying them to production, allowing for more frequent and reliable releases.
- Infrastructure as Code (IaC): IaC tools like Terraform and Ansible allow teams to manage and provision infrastructure using code, making it easier to scale and replicate environments.
- Monitoring and Feedback Loops: DevOps encourages the use of feedback loops, where real-time monitoring data is used to inform ongoing development and operational improvements.
Importance of Deployment and Maintenance:
- User Experience: A smooth deployment ensures that users can access new features without disruption. Ongoing maintenance ensures that the system remains reliable, fast, and secure, providing a better overall user experience.
- Security: Regular updates and patches are critical for addressing security vulnerabilities that can emerge over time. Monitoring tools can also help detect suspicious activity, allowing teams to respond quickly to potential threats.
- Cost Efficiency: Proactively maintaining a system helps prevent major issues that could lead to downtime or expensive fixes. Automation of deployment and maintenance tasks also reduces labor costs and minimizes the risk of human error.
system and software deployment and maintenance are essential for delivering and sustaining high-quality systems and applications. By implementing strategies such as continuous deployment and leveraging monitoring tools, organizations can ensure that their systems perform reliably, remain secure, and meet the needs of their users in a dynamic and ever-changing environment. DevOps practices help automate and optimize these processes, reducing errors and fostering better collaboration across teams.
System and Software Security Engineering
System and Software Security Engineering is an integral part of modern software development, aimed at protecting systems, data, and users from a wide range of threats. Security must be incorporated into the entire software engineering process, from initial design through deployment and maintenance. The cost of ignoring security can be significant, leading to data breaches, operational disruptions, financial loss, and damage to an organization’s reputation.
Here are the key aspects of security in system and software engineering:
1. Cyber Threats:
Cyber threats refer to malicious activities aimed at compromising the integrity, confidentiality, or availability of a system or data. These include:
-
- Hacking: Unauthorized access to a system or network with the intent to steal, alter, or destroy data.
- Malware: Malicious software, such as viruses, ransomware, or spyware, designed to damage or disrupt systems.
- Phishing: Fraudulent attempts to obtain sensitive information, such as passwords or credit card details, by posing as a legitimate entity in electronic communications.
2. Vulnerabilities:
Vulnerabilities are weaknesses or flaws in a system that can be exploited by attackers. These can arise from poor software design, coding errors, outdated software, or misconfigurations. Common vulnerabilities include:
-
- SQL Injection: A code injection technique that allows attackers to manipulate databases by executing unauthorized SQL queries.
- Cross-Site Scripting (XSS): A vulnerability in web applications where attackers inject malicious scripts into web pages viewed by other users.
- Buffer Overflow: An error where a program writes data beyond the buffer’s memory boundary, potentially allowing attackers to overwrite memory and execute malicious code.
3. Security Engineering Best Practices:
To defend against these threats and vulnerabilities, security needs to be an ongoing, integral part of the system and software engineering process. The following best practices are fundamental to building secure systems:
-
- Encryption:
- Definition: Encryption is the process of converting sensitive data into a coded format that can only be deciphered by authorized individuals with the correct decryption key. This ensures that even if data is intercepted by attackers, it cannot be read.
- Types of Encryption:
- Symmetric Encryption: A single key is used for both encryption and decryption.
- Asymmetric Encryption: Two keys are used—one for encryption (public key) and one for decryption (private key).
- Applications: Encryption is widely used to protect sensitive information such as passwords, financial data, and communications. Secure protocols like HTTPS use encryption to protect web traffic.
- Access Control:
- Definition: Access control involves implementing rules and policies that restrict who can view, modify, or use certain resources or data within a system. Effective access control ensures that only authorized personnel have the appropriate level of access.
- Techniques:
- Role-Based Access Control (RBAC): Access is granted based on the user’s role within the organization. For example, a system administrator may have more privileges than a regular user.
- Multi-Factor Authentication (MFA): Requires users to provide two or more verification factors, such as a password and a one-time code sent to their phone, to gain access to a system.
- Example: In a healthcare system, only doctors and authorized medical staff may have access to patient records, while administrative staff may be limited to scheduling information.
- Security Testing:
- Definition: Security testing is the process of evaluating a system for vulnerabilities and weaknesses that could be exploited by attackers. Regular testing ensures that security measures are effective and up-to-date.
- Types of Security Testing:
- Penetration Testing (Pen Testing): Simulating an attack on a system to identify and exploit vulnerabilities, allowing them to be fixed before a real attack occurs.
- Vulnerability Scanning: Automated tools are used to scan systems for known vulnerabilities, such as outdated software or misconfigured settings.
- Code Reviews: Reviewing source code to identify security flaws such as hard-coded passwords, insecure data handling, or improper input validation.
- Example: A financial institution may conduct regular penetration tests on its online banking platform to ensure that it is secure against cyber attacks.
- Encryption:
4. The Importance of Security by Design:
Security engineering must begin during the design phase, rather than being an afterthought. Building security into the architecture from the outset is known as “security by design,” and it ensures that systems are designed with robust protections against threats. Key practices include:
-
- Threat Modeling: Identifying potential security threats during the design phase and planning countermeasures to mitigate them.
- Least Privilege Principle: Ensuring that users and processes have only the minimal access necessary to perform their tasks, reducing the potential damage from a breach.
- Defense in Depth: Implementing multiple layers of security, such as firewalls, encryption, and access controls, to protect against different types of attacks.
5. Security Monitoring and Incident Response:
In addition to preventive measures, it’s essential to have mechanisms in place to detect and respond to security incidents in real-time. Security monitoring involves continuously tracking system activities for signs of malicious behavior or breaches.
-
- Intrusion Detection Systems (IDS): Monitors network traffic for suspicious activity and alerts administrators to potential threats.
- Security Information and Event Management (SIEM): Aggregates data from various sources to provide a comprehensive view of security events and identify patterns that indicate an attack.
- Incident Response: A formal process for managing and responding to security incidents, including containment, eradication, and recovery efforts.
6. The Role of Compliance in Security:
Many industries are subject to regulations and standards that dictate specific security requirements. Organizations must adhere to these compliance frameworks to avoid legal penalties and maintain trust with customers. Common security compliance frameworks include:
-
- GDPR (General Data Protection Regulation): European regulation governing the privacy and protection of personal data.
- HIPAA (Health Insurance Portability and Accountability Act): U.S. regulation governing the security and privacy of health-related information.
- ISO/IEC 27001: An international standard for information security management systems.Security is a critical component of system and software engineering, ensuring that systems remain resilient against cyber threats and vulnerabilities. By employing encryption, access control, and regular security testing, and by adopting a security-by-design approach, organizations can significantly reduce the risk of breaches and maintain the trust of their users. Additionally, ongoing security monitoring and compliance with industry regulations are necessary to safeguard systems in a dynamic threat landscape.
Integrating security into the entire software development lifecycle—rather than treating it as an afterthought—ensures a holistic and robust approach to protecting both systems and data.
How MicroGenesis can help
MicroGenesis offers comprehensive Systems Engineering Solutions designed to help organizations manage the complexity of system development across various industries. By integrating tools and processes, MicroGenesis enables efficient collaboration between stakeholders, ensuring that requirements, design, testing, and validation are seamlessly aligned. Their solutions focus on:
-
- Requirements Management: Ensuring all system requirements are captured, tracked, and met throughout the development lifecycle.
- Model-Based Systems Engineering (MBSE): Using models to define, design, and document systems, allowing for improved system architecture and design decisions.
- Verification & Validation: Ensuring systems are thoroughly tested against requirements, enhancing reliability and performance.
With their expertise in systems engineering, MicroGenesis helps organizations deliver high-quality, compliant, and efficient systems that meet business objectives.
Conclusion
Microgenesis, a leader in systems engineering services and digital transformation, is dedicated to helping businesses navigate these complexities. With a focus on innovative engineering solutions, Microgenesis empowers organizations to leverage the latest technologies and methodologies, ensuring they remain competitive in their respective industries. Partnering with us means embarking on a transformative journey that not only enhances operational efficiency but also drives sustainable growth.
Services


Related posts
How Jira Service Management Fuels Innovation in Hi-Tech & Electronics
The hi-tech and electronics industry is characterized by rapid innovation, complex supply chains, and intense competition. From managing product development...
How Jira Service Management Transforms Efficiency in the Transport & Logistics Industry
In an industry defined by precise coordination, high demand, and strict timelines, transport and logistics companies are under constant pressure to deliver...
How Jira Service Management Empowers Financial Services Companies
Financial services have always been driven by a need for trust, compliance, and high-quality customer service. Today, the demand for faster service delivery...



