Digital transformation has become a buzzword in recent years, as businesses across industries seek to adapt to rapidly evolving technologies and customer expectations. But what exactly is digital transformation? Why is it so crucial for enterprises today, and what are the key areas to focus on? In this comprehensive guide, we’ll dive deep into the concepts, drivers, benefits, and practical frameworks of digital transformation, providing you with the knowledge and insights to embark on this journey with confidence.
What is Digital Transformation?
Digital transformation refers to the integration of digital technology into all areas of a business, fundamentally changing how the organization operates and delivers value to customers. It’s not just about digitizing existing processes, but rather a complete cultural and operational shift towards agility, innovation, and customer-centricity.
The goal is to leverage digital tools, data, and innovation to improve business processes, enhance customer experiences, increase operational efficiency, and open new revenue streams. However, digital transformation is more than a technological upgrade; it’s a profound change in the way companies approach problem-solving, decision-making, and collaboration.
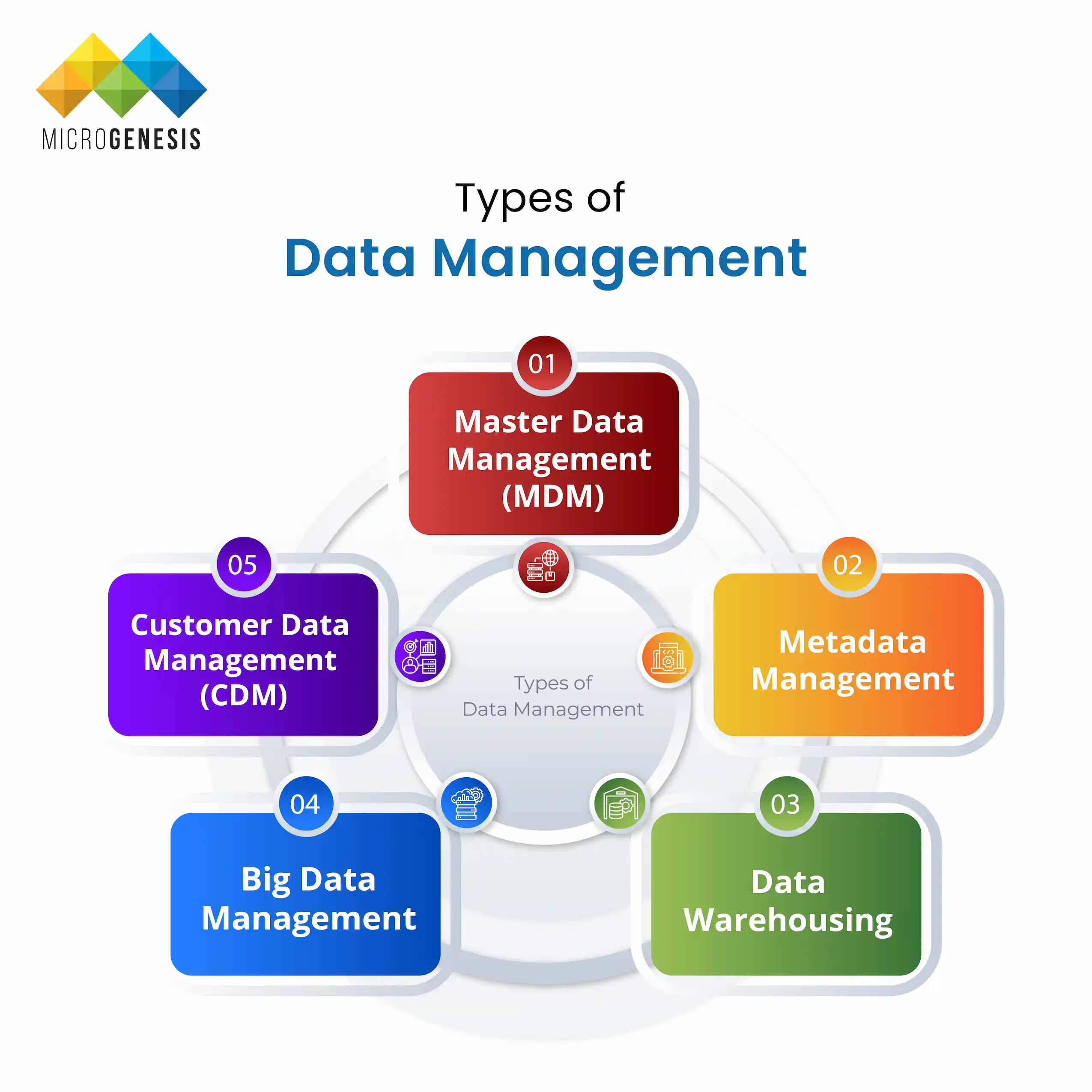
3 Key Areas of Enterprise Digital Transformation
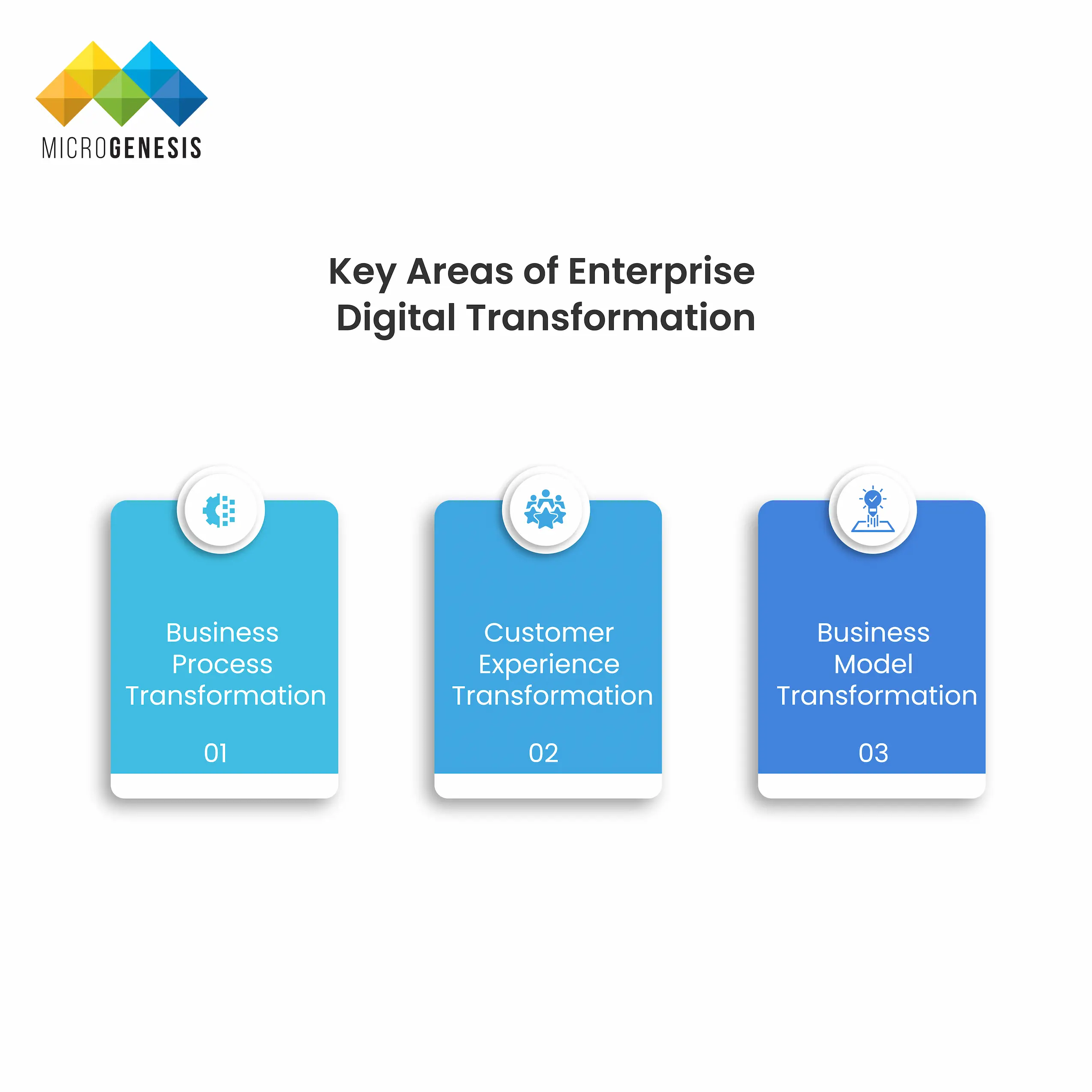
There are three primary areas where businesses need to focus their digital transformation efforts:
1. Business Process Transformation
This involves leveraging digital tools to redesign business operations, enhancing both efficiency and effectiveness. Organizations must move beyond automating simple tasks to fully rethinking workflows and operational structures. Technologies like robotic process automation (RPA), AI, and machine learning can optimize and automate repetitive tasks, enabling employees to focus on higher-value activities.
For example, by automating supply chain operations, manufacturers can improve production efficiency, reduce costs, and increase the accuracy of forecasting demand, thus enhancing overall business performance. Furthermore, AI and data analytics tools help streamline decision-making by delivering real-time insights based on large sets of data.
2. Customer Experience Transformation
The modern customer expects personalized, seamless, and highly responsive interactions with businesses. Delivering exceptional customer experiences is at the heart of digital transformation. To meet these expectations, companies are adopting digital solutions that allow for more meaningful engagement through mobile apps, social media, and chatbots, to name a few.
Companies like Disney have mastered digital customer experience through its MagicBand wristbands, which use RFID technology to enhance guest experience at its theme parks. From seamless access to rides to personalized services, Disney uses data to deliver frictionless, delightful interactions at every touchpoint.
3. Business Model Transformation
In the digital age, businesses must rethink their entire value proposition and revenue models. Digital transformation empowers companies to move beyond traditional product-based sales models and explore new opportunities such as subscription services, digital marketplaces, or service-based models. Cloud computing, AI, and IoT provide the technical foundation for these new revenue streams.
A perfect example of business model transformation is Airbnb. The company disrupted the hospitality industry by creating a peer-to-peer digital platform that connects travelers with private accommodation providers. This model offers a scalable, asset-light business without the need to own real estate, relying instead on technology to facilitate seamless transactions and communications.
What is the Importance of Digital Transformation?

Digital transformation is not optional for businesses seeking to maintain a competitive edge in today’s marketplace. It has become a necessity for companies aiming to stay relevant, agile, and customer-centric. Here are some key reasons why digital transformation is crucial:
1. Meeting Customer Expectations
Today’s customers are empowered, tech-savvy, and connected. They expect fast, personalized, and convenient experiences. Companies that fail to meet these expectations risk losing customers to more digitally mature competitors. A company’s ability to leverage digital tools—such as AI-driven personalization, chatbots, and predictive analytics—will directly impact its ability to attract, retain, and delight customers.
2. Driving Operational Efficiency
Through automation, digital transformation helps companies eliminate redundant tasks, reduce manual errors, and improve speed and precision. This leads to higher productivity and cost savings across all business functions, from supply chain management to human resources. Cloud-based platforms and AI-driven workflows allow businesses to be more agile and responsive to market changes, freeing up resources to focus on innovation and strategy.
3. Enabling Innovation and Adaptability
In a rapidly changing business environment, companies must remain agile to survive. Digital transformation fosters a culture of innovation by encouraging experimentation and the adoption of new technologies. Businesses that invest in digital tools can quickly pivot to address new opportunities, whether through the development of new products, services, or revenue models.
4. Gaining Competitive Advantage
A company that undergoes digital transformation is better positioned to outperform competitors that lag in adopting digital tools. For example, businesses that leverage predictive analytics can identify market trends faster, allowing them to make smarter decisions before competitors even recognize a shift.
5. Future-Proofing the Organization
Digital transformation prepares businesses to navigate an uncertain future. It enables them to adapt to new technologies, emerging markets, and regulatory changes more efficiently. A future-proof organization is one that embraces digital innovation as a continual process, rather than a one-time initiative.
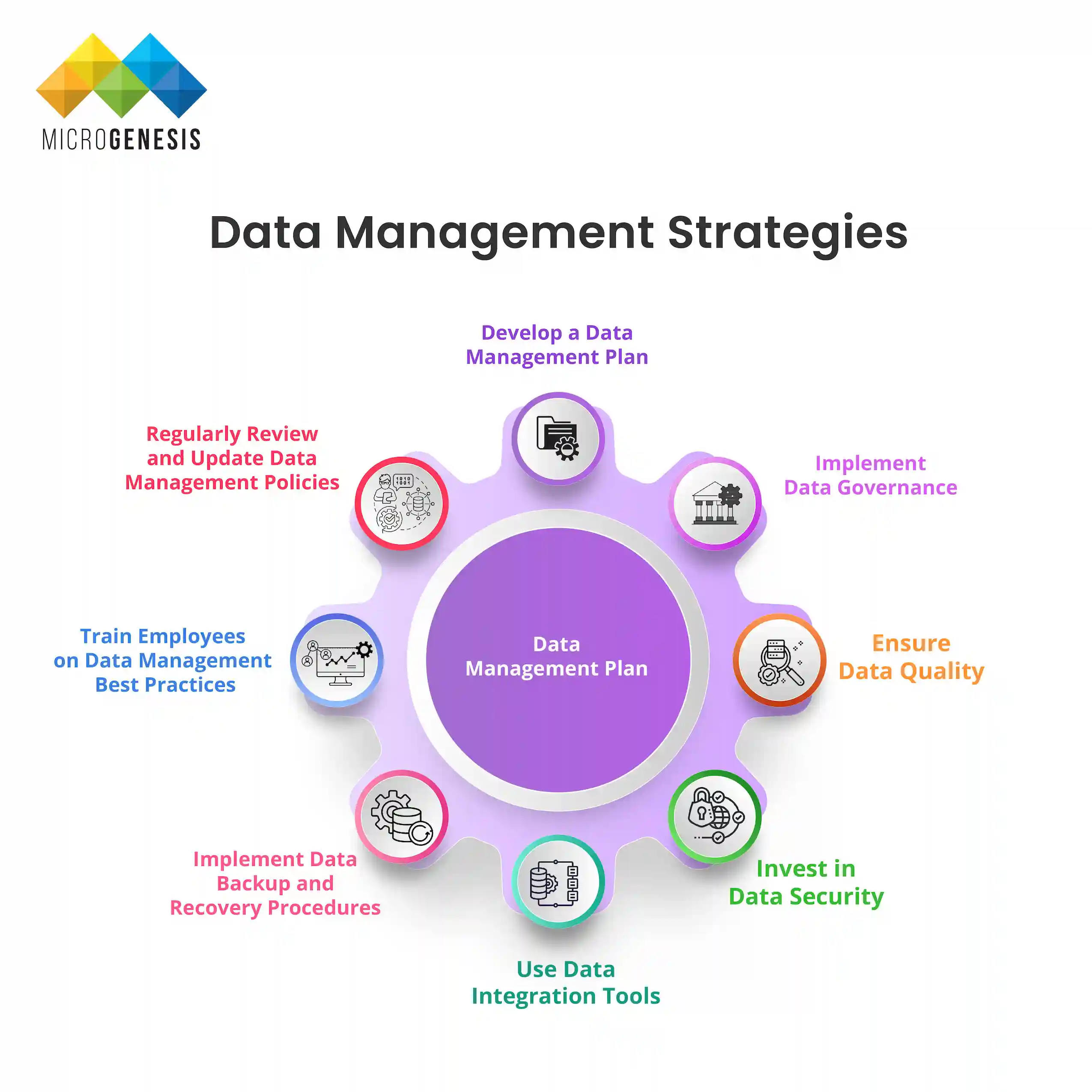
What Does a Digital Transformation Framework Look Like?
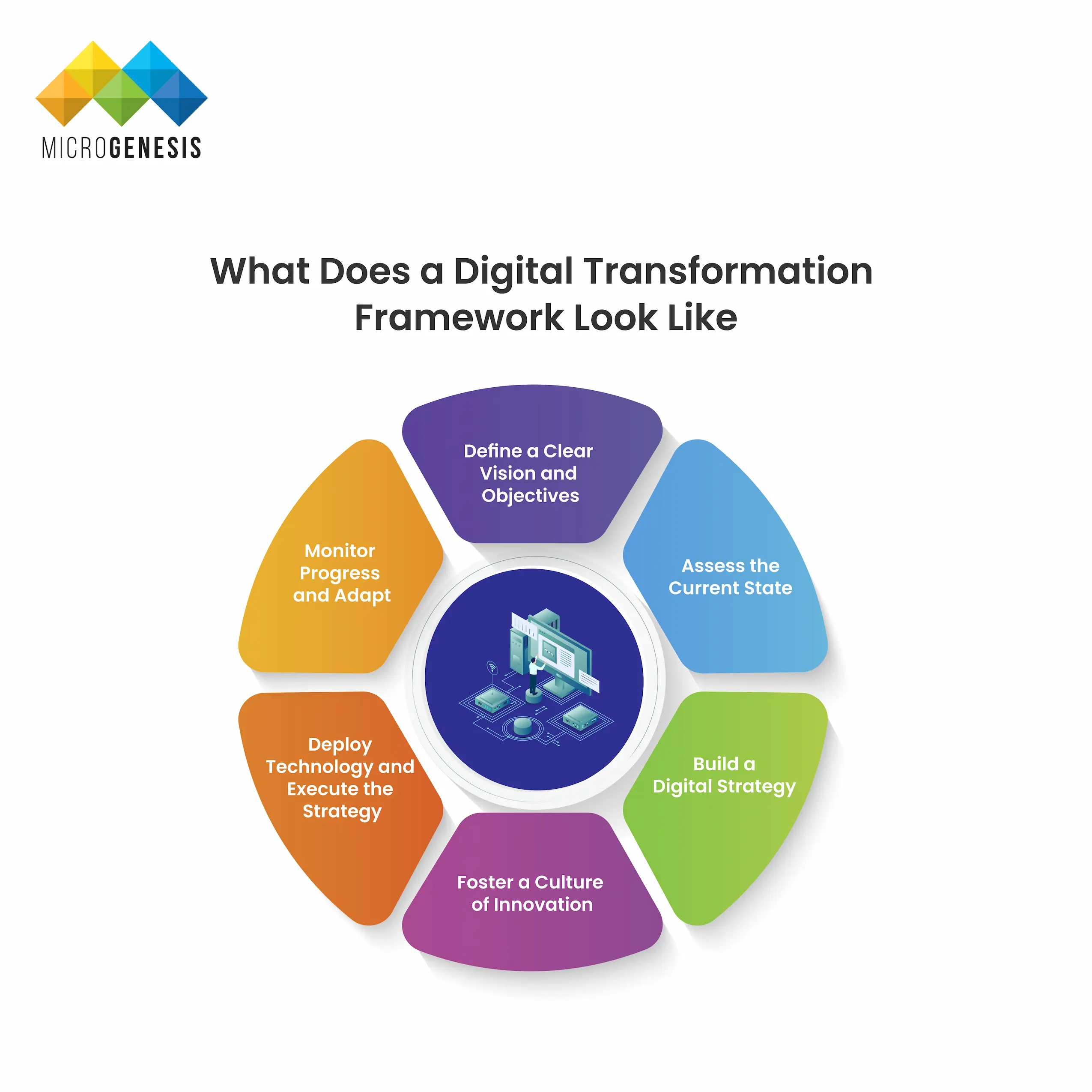
A digital transformation framework is a structured approach that helps organizations navigate the complexities of integrating digital technologies into their core business. A well-defined framework guides the organization through the different stages of transformation and ensures alignment with business goals. Here’s a general outline of a robust digital transformation framework:
1. Define a Clear Vision and Objectives
Before embarking on the digital transformation journey, leaders must clearly articulate their vision. What are the primary goals? Whether it’s enhancing customer experience, improving operational efficiency, or driving new revenue streams, having a well-defined set of objectives is essential to align the entire organization.
2. Assess the Current State
Understanding the current state of the business is crucial. This includes assessing the existing technology infrastructure, analyzing workflows, and evaluating employee digital skills. Conducting a gap analysis helps to identify areas that require digital upgrades or process changes.
3. Build a Digital Strategy
Once gaps are identified, a comprehensive digital strategy should be developed. This strategy should map out the technologies, processes, and skills needed to achieve the desired outcomes. It should also include a timeline, budget, and key performance indicators (KPIs) for measuring success.
4. Foster a Culture of Innovation
Technology alone cannot drive transformation. People are at the heart of digital change. A culture of innovation—where employees are encouraged to embrace new technologies, take calculated risks, and continuously learn—is crucial for a successful digital transformation. Leaders must foster an open, agile environment where experimentation and learning from failures are embraced.
5. Deploy Technology and Execute the Strategy
Once the strategy is in place, the next step is to deploy the right technologies to support it. Cloud computing, AI, big data, IoT, and automation tools are just a few examples of technologies that can drive transformation. The deployment should be phased, allowing the organization to address challenges incrementally and measure success.
6. Monitor Progress and Adapt
Digital transformation is not a one-time project but a continuous process. Organizations must continuously monitor their progress using KPIs and adapt their strategy as they evolve. This ensures that the digital transformation effort remains aligned with business goals and market trends.
What Drives Digital Transformation?

Digital transformation is driven by several key factors that compel organizations to rethink the way they operate. Here are the primary drivers:
1. Technological Advancements
The rapid pace of technological innovation is one of the most significant drivers of digital transformation. Emerging technologies such as AI, machine learning, blockchain, IoT, and cloud computing offer businesses new ways to create value, streamline operations, and engage with customers. Companies that fail to adopt these innovations risk falling behind competitors.
2. Changing Consumer Behavior
Today’s consumers are digital-first. They expect personalized, immediate, and seamless interactions with brands across various channels. Businesses must adopt digital strategies to meet these evolving expectations, or they risk losing market share to more agile competitors.
3. Industry Disruption
Many industries are being disrupted by digital-native startups that leverage technology to deliver better customer experiences, lower prices, or more innovative products. Companies must undergo digital transformation to stay competitive in the face of new entrants.
4. Regulatory Requirements
In industries such as healthcare, finance, and insurance, regulatory compliance often drives digital transformation. Digital tools can streamline reporting, ensure data security, and help organizations comply with evolving regulations more efficiently.
5. Globalization
Digital tools enable businesses to operate on a global scale with relative ease. Organizations can use digital platforms to engage with customers in new markets, scale their operations, and collaborate with international partners more effectively.
The Benefits of Digital Transformation
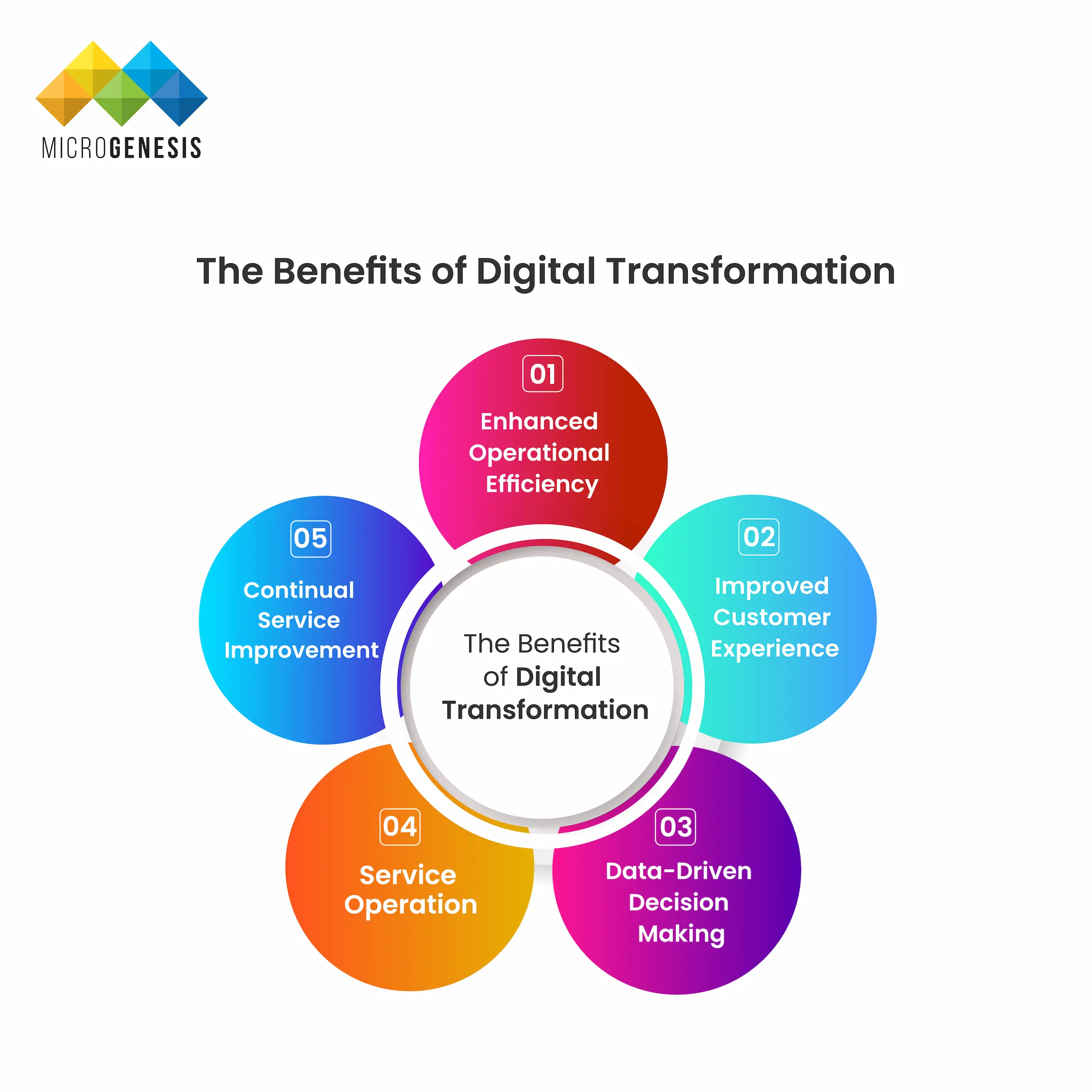
Digital transformation offers a wide range of benefits that extend across an organization’s operations, customer interactions, and long-term growth. These include:
1. Enhanced Operational Efficiency
By automating routine tasks, digitizing workflows, and leveraging data analytics, organizations can significantly improve operational efficiency. Manual processes that once took days or weeks can now be completed in minutes, reducing errors, enhancing accuracy, and speeding up decision-making.
2. Improved Customer Experience
With the integration of digital tools such as customer relationship management (CRM) systems, AI-driven chatbots, and personalized marketing platforms, businesses can better understand customer preferences and deliver more tailored experiences. This personalization leads to higher customer satisfaction and loyalty.
3. Data-Driven Decision Making
One of the key advantages of digital transformation is the ability to harness vast amounts of data from various sources. By leveraging data analytics tools, businesses can extract actionable insights to make informed, data-driven decisions. This helps in optimizing operations, identifying new market opportunities, and improving customer service.
4. Increased Agility and Innovation
Digital transformation encourages a culture of agility and continuous improvement. Businesses that embrace digital tools can quickly respond to changes in the market, emerging technologies, and customer demands. This flexibility allows them to innovate faster and more effectively.
5. Cost Savings and Revenue Growth
Automating processes and optimizing workflows not only leads to cost savings but also frees up resources that can be redirected toward growth initiatives. Digital transformation also opens up new revenue opportunities through digital channels, subscription services, and other innovative business models.
6. Stronger Competitive Advantage
Organizations that embrace digital transformation are better positioned to stay ahead of their competition. By adopting cutting-edge technologies, businesses can offer unique value propositions, deliver superior customer experiences, and optimize their operations more efficiently than their competitors.
Examples of Digital Transformation
Many companies have successfully navigated their digital transformation journeys, offering valuable lessons for others:
Netflix transformed from a DVD rental service into a global streaming platform, leveraging digital technologies to change the way people consume media. Their use of data analytics to offer personalized content recommendations has been a significant driver of customer satisfaction and growth.
Amazon’s digital transformation is one of the most notable in history. They revolutionized e-commerce by adopting advanced logistics, AI-driven recommendations, and cloud computing to create a seamless online shopping experience.
GE transformed its industrial equipment business by adopting IoT and predictive analytics. Their “Industrial Internet” platform allows machines to communicate, providing data insights that enhance performance and reduce downtime.
Most Important Aspects of Digital Transformation
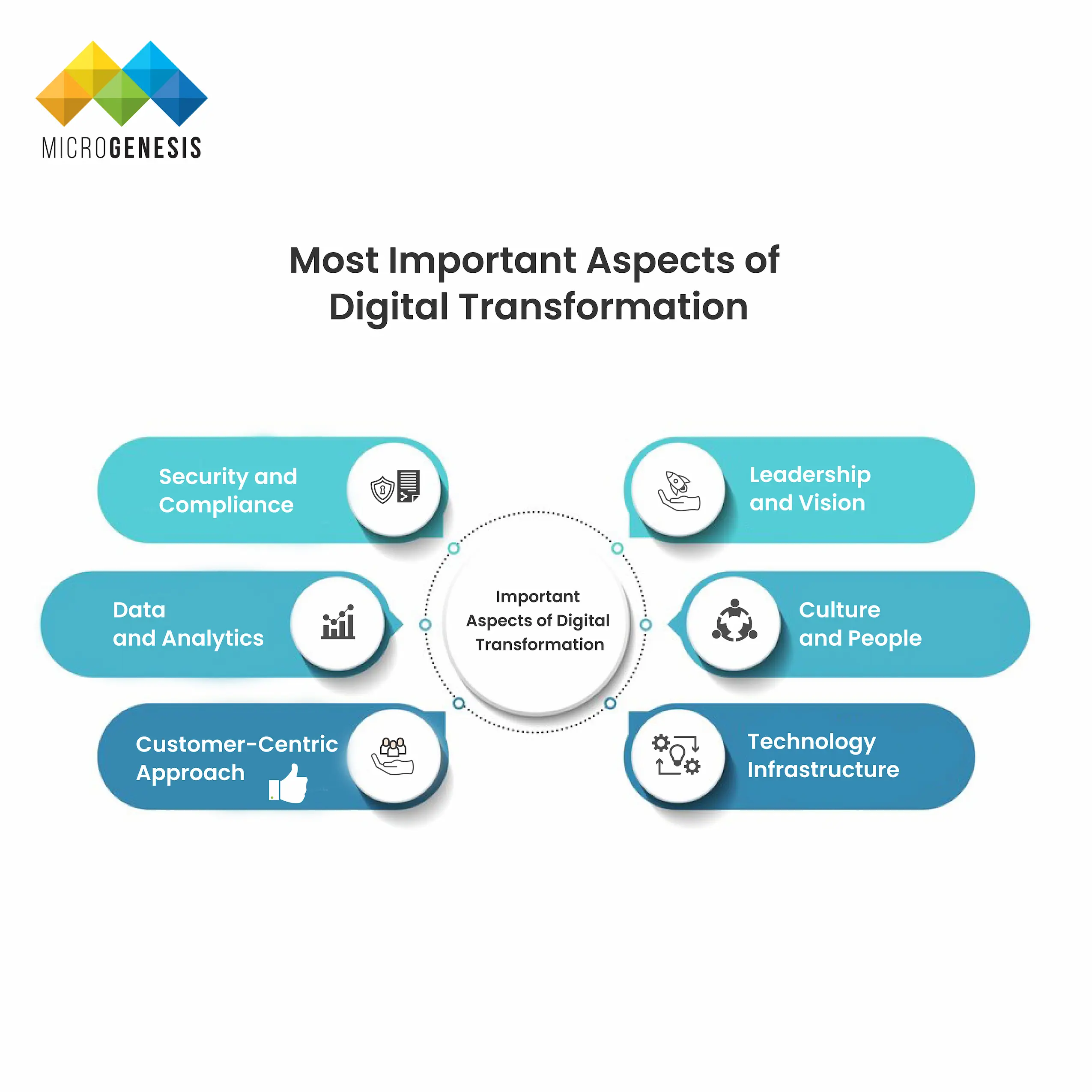
Digital transformation is a complex process that touches every part of an organization. Here are some of the most important aspects to focus on:
1. Leadership and Vision
Successful digital transformation requires strong leadership and a clear vision. Leaders must champion digital initiatives, communicate the importance of transformation to the organization, and guide employees through the changes. Leadership buy-in is critical for driving cultural change and securing the resources needed for transformation efforts.
2. Culture and People
People are at the heart of digital transformation. Organizations must foster a culture of innovation, agility, and continuous learning. Employees need to be empowered to embrace new technologies and rethink traditional workflows. Upskilling and reskilling initiatives are also vital to ensure employees have the digital skills required to thrive in a transformed workplace.
3. Technology Infrastructure
Investing in the right technology is critical for driving transformation. Cloud computing, data analytics, artificial intelligence, and IoT are just a few examples of technologies that can power digital initiatives. It’s essential to have a scalable, secure, and adaptable IT infrastructure in place to support ongoing transformation.
4. Customer-Centric Approach
At the end of the day, digital transformation is about delivering value to customers. Companies must adopt a customer-first mindset and leverage technology to provide personalized, seamless, and engaging experiences. Whether it’s through personalized marketing, AI-driven chatbots, or self-service portals, the goal is to create experiences that meet customers’ evolving needs.
5. Data and Analytics
Data is a key enabler of digital transformation. Businesses must harness the power of data to gain insights into customer behavior, operational efficiency, and market trends. Advanced data analytics, predictive modeling, and machine learning can help organizations make data-driven decisions that drive better outcomes.
6. Security and Compliance
With the rise of digital transformation comes the increased importance of data security and regulatory compliance. Organizations must implement robust security measures to protect customer data and intellectual property from cyber threats. Compliance with industry regulations such as GDPR, HIPAA, or PCI-DSS is also crucial in avoiding legal and financial penalties.
How Can I Measure ROI on Digital Transformation?
Measuring the return on investment (ROI) of digital transformation can be challenging, given its wide-ranging impact across multiple areas of the business. However, it is crucial for justifying investment in digital initiatives and ensuring that the transformation is delivering value. Here are some key metrics to consider:
1. Operational Efficiency
One of the most straightforward ways to measure ROI is through increased operational efficiency. By tracking the time saved from automated processes, reduced error rates, and lower costs, you can quantify the gains made from digital transformation. For example, you can measure the reduction in manual tasks or time taken to complete key processes before and after automation.
2. Revenue Growth
Track the impact of digital transformation on revenue growth. This could be through the adoption of new digital business models, the launch of new digital products, or the expansion into new markets via digital channels. Compare revenue growth pre- and post-transformation to gauge the financial impact.
3. Customer Experience
Improvements in customer experience often translate to increased customer satisfaction, retention, and lifetime value. Use metrics such as Net Promoter Score (NPS), customer satisfaction ratings, and churn rates to measure the impact of digital transformation on customer loyalty and engagement.
4. Employee Productivity
Digital transformation often leads to significant improvements in employee productivity. You can measure this through metrics such as task completion time, the number of projects completed, or the number of clients served within a given period. These productivity gains can directly impact the organization’s bottom line.
5. Innovation and Agility
Assess the organization’s ability to innovate and adapt to market changes post-transformation. This can be measured by tracking the time taken to develop and launch new products, the number of new initiatives started, and the speed at which the organization can pivot in response to new opportunities or challenges.
6. Cost Savings
Cost savings are another critical measure of ROI. By comparing costs before and after digital transformation initiatives, particularly in areas such as IT infrastructure, supply chain management, and customer support, you can calculate the financial impact of digitization.
Why Digital Transformation Projects Fail
Despite the many potential benefits, digital transformation projects often fail to deliver on their promises. Here are some common reasons why:
1. Lack of Clear Vision and Strategy
Without a well-defined vision and strategy, digital transformation efforts can lack direction and coherence. It’s essential to have a clear understanding of the business objectives and how digital tools will help achieve them. Otherwise, transformation efforts may result in disjointed initiatives that fail to deliver value.
2. Resistance to Change
People are naturally resistant to change, and this can be a major barrier to digital transformation. Employees may fear that new technologies will render their skills obsolete, or they may be uncomfortable with changes to established workflows. Overcoming this resistance requires strong leadership, clear communication, and investment in training and development.
3. Underestimating the Complexity
Digital transformation is a complex, multi-faceted process that affects every part of an organization. Many companies underestimate the time, effort, and resources required to execute a successful transformation. Over-simplifying the process or expecting quick results can lead to failure.
4. Failure to Align with Business Goals
If digital transformation efforts aren’t aligned with broader business goals, they may end up as isolated IT projects that don’t deliver real value. For example, implementing AI tools without a clear understanding of how they will improve customer service or operational efficiency can result in wasted resources and missed opportunities.
5. Lack of Employee Buy-In
Without employee buy-in, even the best digital strategies will fail. It’s important to involve employees in the digital transformation process from the beginning, addressing their concerns and highlighting how digital tools will benefit them in their roles.
6. Inadequate Budget and Resources
Digital transformation requires significant investment in both technology and people. A lack of budget or underestimation of the resources required can doom a digital transformation project to failure before it even begins.
How to Get Started with Digital Transformation
For companies that haven’t yet begun their digital transformation journey, starting can feel overwhelming. Here are practical steps to get started:
1. Assess Your Current Digital Maturity
Before embarking on digital transformation, it’s important to understand where your company currently stands. Conduct a digital maturity assessment to evaluate your existing technology stack, digital skills, and processes. Identify the areas that require the most improvement.
2. Set Clear Objectives
Define your transformation goals clearly. Are you looking to enhance customer experiences, improve operational efficiency, or create new revenue streams? Setting clear objectives will help focus your efforts and ensure alignment with broader business goals.
3. Build a Cross-Functional Team
Digital transformation affects every part of an organization, so it’s important to have a cross-functional team leading the effort. This team should include representatives from IT, marketing, operations, HR, and other departments to ensure a holistic approach.
4. Start with Small Pilot Projects
Rather than trying to transform the entire organization all at once, start with small pilot projects. These projects can provide quick wins and demonstrate the value of digital transformation to stakeholders. Once successful, these initiatives can be scaled across the organization.
5. Invest in Digital Skills
Digital transformation requires a workforce that is comfortable using digital tools and technologies. Invest in upskilling and reskilling initiatives to ensure your employees have the digital skills needed to thrive in a transformed organization.
6. Monitor Progress and Adjust
Digital transformation is an ongoing process. Continuously monitor the progress of your initiatives and adjust your strategy as needed. Use KPIs to measure success and ensure that transformation efforts are delivering real value.
Digital Transformation Trends
Here are some of the latest trends in digital transformation that are shaping the future of business:
1. Artificial Intelligence and Machine Learning
AI and machine learning continue to be major drivers of digital transformation. From personalized marketing and customer service chatbots to predictive analytics and automation, AI is enabling businesses to operate more efficiently and deliver superior customer experiences.
2. Cloud Computing
Cloud adoption is accelerating as businesses look for scalable, flexible, and cost-effective solutions to power their digital initiatives. Cloud platforms provide the foundation for other digital technologies, enabling businesses to access computing resources on-demand and scale as needed.
3. 5G Technology
The rollout of 5G networks is expected to revolutionize industries by providing faster, more reliable internet connections. This will enable new digital transformation opportunities, such as enhanced IoT applications, autonomous vehicles, and real-time analytics.
4. Digital Twins
Digital twins are virtual replicas of physical assets, processes, or systems that use real-time data to simulate performance. This technology is being used in industries such as manufacturing, healthcare, and logistics to optimize operations, reduce downtime, and improve product development.
5. Cybersecurity
As digital transformation accelerates, the need for robust cybersecurity measures has never been more important. Companies are increasingly investing in advanced cybersecurity solutions to protect against data breaches, cyber-attacks, and compliance risks.
Here are some excellent resources for further learning:
- Books: “Digital Transformation Playbook” by David Rogers, “Leading Digital” by George Westerman, Didier Bonnet, and Andrew McAfee
- Websites: McKinsey & Company, Deloitte Insights, and Harvard Business Review
- Online Courses: Coursera’s “Digital Transformation” courses, edX’s “Leading Digital Transformation” programs
Digital transformation is more than just adopting new technologies—it’s a fundamental shift in how businesses operate, innovate, and deliver value to their customers. By integrating digital tools and fostering a culture of agility and customer-centricity, companies can streamline processes, improve customer experiences, and unlock new growth opportunities. However, successful digital transformation requires a clear strategy, strong leadership, and a willingness to embrace change at every level of the organization.
Microgenesis, as a digital transformation consultant, specializes in guiding businesses through this complex process. With tailored strategies and deep industry expertise, Microgenesis helps companies not only implement the right technologies but also foster the cultural and operational shifts needed for long-term success in the digital era
1.What is digital transformation in simple terms?
It’s the integration of digital technology into all areas of business, changing how businesses operate and deliver value to customers.
2.How long does digital transformation take?
It varies but typically takes several years, depending on the scale of transformation.
3.Is digital transformation only about technology?
No, it’s also about changing the culture, processes, and business models to fully leverage technology.
4.What is the role of leadership in digital transformation?
Leadership plays a critical role in setting the vision, securing buy-in, and driving the cultural shift necessary for transformation.